online shopping and leisure activities.
The Role of Artificial Intelligence in Personalization
AI plays a crucial part in advancing bespoke experiences within dynamic recommendation models. By processing extensive data, AI algorithms can uncover patterns and trends that influence user decisions.
AI greatly improves personalization in recommendation systems by examining data to reveal user preferences.
This technology enables the delivery of personalized content, products, or offerings based on specific actions, environment, and past interactions. Machine learning systems regularly update based on recent developments, refining the relevance of suggestions over the years.
In addition, AI facilitates immediate data assessment, allowing for immediate modifications based on user involvement and outside influences. Through these capabilities, artificial intelligence transforms standard services into customized interactions, ultimately driving customer satisfaction and loyalty.
Therefore, organizations using AI for personalization can better meet the diverse needs of their audience, fostering deeper connections.
How Keytalk Analyzes User Preferences
Keytalk employs sophisticated algorithms to analyze user activity patterns, providing clarity into personal preferences.
By grasping these models, the platform can effectively tailor content delivery to increase user engagement.
This unique customized strategy promises that suggestions remain pertinent and prompt, addressing the specific preferences of every user.
Analyzing User Behavior Patterns
During the engagement of users with digital platforms, their behavior patterns reveal valuable insights into likes and dislikes.
Keytalk leverages cutting-edge analytics to monitor user engagements, such as click-throughs, duration spent on particular content, and navigation paths. By analyzing these data points, Keytalk identifies patterns and common traits among participants, helping to form a robust profile of unique preferences.
This examination not only emphasizes popular features and content but also discovers lesser-known interests that might need acknowledgment. By observing transitions in behavior over time, Keytalk can refine its strategies, ensuring that suggestions remain applicable and current.
Ultimately speaking, understanding user behavior patterns facilitates Keytalk to tailor its approach, boosting the overall user experience on digital platforms.
Customized Content Distribution
Ensuring content connects with users, individualized content delivery is fundamentally based on analyzing individual preferences. Keytalk makes use of innovative algorithms for the interpretation of user data, enabling the platform to tailor content dynamically. This technique confirms that users receive suitable recommendations that correspond to their individual interests and behaviors.
Keytalk evaluates user preferences using different techniques, such as:
- User Interaction Records: Analyzing engagement metrics and click data.
- User Demographic Information: Evaluating age, locality, and gender.
- Content Consumption Patterns: Spotting commonly accessed subjects.
- User Feedback Techniques: Incorporating user reviews and feedback.
- Activity on Social Media: Investigating social media shares and likes for added clarity.
Determinants of Suggestions
Recognizing the various aspects that impact recommendations is crucial for improving the efficiency of AI-driven systems. A range of factors adds to the quality of recommendations, including customer behavior, preferences, and historical interactions.
Data about context, like the time of day, the location, and the device employed, greatly impacts bespoke recommendations. Additionally, demographic information and social factors can further refine the recommendations presented to users.
AI algorithms examine these variables to uncover trends and forecast user choices, ensuring that the suggestions stay pertinent and up-to-date. The integration of broad data origins ultimately enhances the overall user experience, making the recommendations better customized and impactful in addressing personal requirements.
Enhancing User Engagement Through Tailored Suggestions
Tailor-made tips can greatly enhance user engagement by delivering personalized content that resonates with individual preferences.
By leveraging contextual user insights, platforms can create experiences that hold greater relevance that capture attention and encourage interaction.
This technique not only nurtures a greater connection with users but also raises the odds of continual engagement.
Customized Content Provision
As users move through the broad online landscape, bespoke content sharing emerges as an essential strategy for enhancing engagement. By tailoring suggestions based on individual preferences and behaviors, platforms can effectively increase user satisfaction and loyalty.
This approach not only fosters deeper connections but also drives higher conversion rates.
Crucial components of customized content delivery are:
- Analysis of User Behavior: Observing user actions to identify preferences.
- Real-Time Recommendations: Offering suggestions in real-time according to latest trends.
- User Grouping: Grouping users by interests to tailor content effectively.
- User Feedback Channels: Soliciting user feedback to fine-tune suggestions.
- Machine Learning Algorithms: Employing sophisticated analytics to forecast user demands.
Collectively, these factors offer a more stimulating and meaningful experience that appeals to users.
Contextual Insights on User Behavior
Although user preferences influence the way content is delivered, user context information optimize the process of personalization by considering the surroundings in which users utilize platforms.
These insights encompass factors such as venue, daily timing, device category, and even community context, allowing for a more nuanced understanding of user patterns. By analyzing this content, AI systems can generate personalized recommendations that resonate with users in live scenarios, thereby improving engagement.
By way of example, a user browsing a travel site during their lunch break might receive suggestions for destinations that align with their temporary travel intentions.
Consequently, user-specific insights bridge the gap between rigid preferences and adaptive user experiences, fostering enhanced relationships and enhancing the probability of involvement with proposed content.
Keytalk's Technology in Action
The advancements from Keytalk has found a range of applications across different sectors, transforming how businesses engage with their audience. By leveraging adaptive recommendations, companies can enhance user engagement and drive business growth.
Noteworthy applications encompass:
- Digital Commerce: Custom shopping interactions based on user behavior and preferences.
- Lodging and Travel: Tailored travel suggestions and itinerary planning for individual travelers.
- Health Industry: Tailored health solutions and treatment plans based on patient data.
- Show Business: Personalized content suggestions for streaming services, improving viewer satisfaction.
- Retail: Enhanced in-store experiences through location-based promotions and offers.
These tools showcase Keytalk's capability to improve customer interactions, making them much more impactful and influential across various sectors.
Keytalk's advancements enhance customer interaction, promising that interactions are more relevant and successful across various industries.
The acceptance of this technology points to a shift towards a more personal business atmosphere.
Benefits of Personalized Contextual Recommendations
Recommendations that are context-aware provide significant gains by boosting the user experience through individualized tips.
They support personalization at a massive scale, allowing firms to respond to individual preferences adeptly.
Thus, this strategy brings about boosted interaction metrics because users encounter more applicable content and products.
Improved User Experience
As individuals move through digital platforms, getting customized recommendations that fit their individual contexts enriches their entire experience.
Context-sensitive advice facilitate a hassle-free interaction, confirming that users discover meaningful content without difficulty. This leads to a more engaging and pleasurable user journey.
Key benefits include:
- Improved Relevance: Proposals are tailored to present demands and interests.
- Effective Use of Time: Users save time searching for appropriate content.
- Greater Engagement: Tailored suggestions encourage more meaningful connections.
- Greater Satisfaction: People experience recognition and worth through the platform.
- Boosted Retention: Satisfactory encounters motivate individuals to come back often.
Personalization for Everyone
As many digital platforms seek to create bespoke experiences, achieving personalization at scale remains a substantial obstacle.
Context-sensitive suggestions use intelligent systems to analyze the behavior of users, preferences, and situational factors, enabling a tailored approach that fits specific needs. This technology supports the delivery of pertinent content and offerings, enhancing user contentment and commitment.
Leveraging extensive data, organizations can spot patterns that inform more informed decisions and recommendations. Consequently, businesses can reach a variety of customer segments more successfully, leading to enhanced conversion rates along with customer retention.
Ultimately, the deployment of context-aware recommendations allows for a more engaging user experience, linking user preferences and mass application, effectively redefining how marketers reach their target audiences.
Higher Engagement Levels
In what ways can organizations effectively boost user engagement in an increasingly competitive digital landscape?
Context-aware recommendations powered by advanced algorithms serve as a effective means to enhance engagement with users. By providing personalized suggestions based on user behavior and likes, businesses can promote greater engagement.
The advantages of these suggestions include:
- Improved consumer satisfaction through effective content dissemination.
- Enhanced sales conversions since users encounter solutions that fit their needs.
- Boosted retention rates thanks to personalized engagements driving return customers.
- Increased customer loyalty arising from satisfying user engagements.
- Improved awareness of consumer actions, leading to improved marketing tactics.
Including dynamic suggestions can greatly transform consumer interaction and boost business outcomes.
Keytalk's Algorithm Uncovered
In the world of context-aware recommendations because of its creative method of combining user activities and environmental factors.
By employing advanced machine learning methods, the algorithm examines real-time data, including location, timestamp, and user activities, to produce tailored proposals. This dynamic adaptability allows Keytalk to develop its analyses on an ongoing basis, enhancing user experience.
Also, the algorithm leverages collaborative filtering and content-based methods, ensuring a thorough understanding of user preferences. The result is a sophisticated system capable of delivering individualized suggestions that resonate with users on various dimensions.
By integrating collaborative filtering and content-based strategies, the algorithm fosters a comprehensive understanding of user preferences for custom recommendations.
Keytalk prioritizes context, which significantly boosts accuracy and encourages greater engagement, making it a pivotal tool in the landscape of AI-driven recommendation systems.
Anticipated Trends in AI-Driven Personalization
The growth of intelligent context-aware algorithms, like those used by Keytalk, establishes the foundation for future trends in AI-enabled personalization.
With the development of technology, a number of key trends are poised to arise:
- Superior User Profiling: Using detailed insights into user conduct and desires.
- Instant Adaptation: Models that tailor recommendations immediately according to live statistics.
- Multi-Modal Interaction: Merging vocal, textual, and visual interfaces for a hassle-free experience.
- Data Privacy Centered Approaches: Reconciling individualized services with ensuring user privacy and data safety.
- Universal Synchronization: Offering standardized recommendations over a range of devices and interfaces.
These insights point to a change in favor of more instinctive and user-centered personalization, ultimately boosting the general user experience.
Getting Started With Keytalk's Recommendations
Exploring the effectiveness of Keytalk's recommendations commences with comprehending its sophisticated algorithm constructed to assess user context reliably. This algorithm utilizes diverse data points, including user actions, choices, and up-to-date situations, to deliver personalized suggestions.
To get started, users should integrate Keytalk's API into their applications, enabling effortless data sharing. Post-installation, it's important to establish user profiles and adjust settings for better recommendations. Periodically revising these profiles elevates the algorithm's correctness as time goes on.
Moreover, employing analytics tools provided by Keytalk allows track engagement and refine recommendations further. By following these steps, businesses have the capability to leverage the power of context-sensitive suggestions, ultimately improving user interaction and driving engagement.
Keytalk's unique method sets a new standard in individualized engagements.
Frequently Asked Questions
How is User Data Privacy and Security Ensured by Keytalk?
How companies guarantee user user data protection and protection is critical in today's technological world.
Keytalk uses advanced encryption methods to safeguard sensitive information and adheres to strict data protection regulations.
Additionally, they implement regular security audits and apply anonymization techniques to safeguard user identities.
Am I Able to Tailor My Recommendation Settings in Keytalk?
Can individuals effectively adapt their experiences to suit their desires? In the domain of suggestion algorithms, customization is often a key feature.
Users are able to personalize their recommendation settings, allowing for a more customized experience. This flexibility enables users to modify the types of suggestions they receive, ensuring that the content suits their interests and needs.
In the end, this level of customization enhances customer happiness and engagement within the platform.
Is Keytalk Supported Across All Devices and Platforms?
One compatibility of Keytalk with various devices and applications is an necessary point for prospective users.
Typically, it is built to function effortlessly across various software environments and devices, including handheld devices, portable tablets, and notebooks.
That said, exact compatibility may hinge on the device's specifications and the software version.
Users are encouraged to check the official documentation for detailed information regarding platforms we offer support for to guarantee full functionality.
Update Schedule for Recommendations by Keytalk
This frequency of updates for suggestions varies utilizing the specific methods and details employed.
Usually, systems like Keytalk aim to refresh their recommendations in immediate time or at scheduled intervals to guarantee significance. This may involve ongoing learning from user actions and choices.
Which Industries Stand to Benefit From Keytalk's Context-Aware Suggestions?
Several fields can greatly improve through context-aware recommendations, for example, retail, where individualized shopping encounters enhance customer satisfaction.
Medical professionals can adopt personalized advice to improve patient care and treatment choices.
As well, the hospitality industry can improve guest experiences through individualized service recommendations.
Moreover, education can leverage these insights to provide customized learning pathways for students, making the advice applicable across various fields that prioritize user engagement and satisfaction.
In Conclusion
Within the dynamic world of digital engagement, Keytalk emerges as a lighthouse, guiding users through the fog of information with intelligent recommendations. By harnessing the power of AI technology, it tailors suggestions that resonate deeply with personal tastes, much like a skilled artist who news paints a unique portrait for each admirer. As the tides of individualization continue to rise, Keytalk stands poised to illuminate pathways, enhancing The automation of PKI is vital for ensuring digital advancement. It streamlines the process of managing certificates, reduces manual errors, and enhances security for digital assets. Keytalk offers cutting-edge solutions that facilitate smooth workflow automation and robust protection protocols. By integrating these solutions, organizations can improve oversight, visibility, and operational effectiveness. This proactive approach not only mitigates risks but also positions businesses for long-term growth. Discover how to leverage these pros further for enhanced transformation in the digital landscape. Despite its seemingly complicated nature, Public Key Infrastructure (PKI) is crucial it is critical for ensuring the security of digital communications. PKI functions as a structure for the creation, administration, and dissemination of online certificates, which authenticate the identities of users, devices, and services. PKI is primarily based on asymmetric cryptography, making use of two keys: a publicly available key and a securely kept private key. This two-key system ensures data confidentiality and integrity during transmission. PKI encompasses various components, including Certificate Authorities (CAs) that issue certificates and Registration Authorities (RAs) that verify identities. PKI automation plays an essential role in modern digital infrastructures by streamlining efficient handling of certificates, guaranteeing organizations can adeptly address their cryptographic necessities. This automation improves security protocols by reducing human mistakes and keeping certificates current, thus safeguarding private data. Moreover, it contributes to reduced operating expenses, allowing businesses to utilize resources better. Effective management of certificates is imperative for organizations wishing to boost their digital security profile in a world of increasing technological complexity. Robust Public Key Infrastructure automation facilitates organizations to effectively handle the lifecycle of online certificates, lowering risks and raising operational efficiency. Essential benefits feature: Enhancing security measures is essential for organizations maneuvering the complexities of digital interactions. PKI automation is key in reinforcing a company's security framework. Through the automation of issuing, renewing, and revoking certificates in digital form, businesses can confirm that their communications and transactions remain secure. This automation lessens the risks of errors caused by humans and minimizes the potential for security breaches associated with non-automated tasks. Additionally, PKI automation enables organizations to implement more robust authentication methods, making sure that only authorized users gain access to sensitive information. As online threats become increasingly sophisticated, embracing PKI automation not only strengthens security but also fosters trust among stakeholders, paving the way for a improved cybersecurity framework. Automating Public Key Infrastructure (PKI) not only improves security but also greatly reduces costs of operation for organizations. Through improving workflows and decreasing manual intervention, PKI automation offers various financial pros: Incorporating PKI automation allows organizations to allocate resources more effectively, ultimately driving down operational expenses and supporting digital growth. Keytalk delivers advanced solutions that simplify administration of certificates, facilitating the management of digital credentials for organizations. The organization’s augmented security systems greatly enhance the integrity of these systems, ensuring security from potential threats. In addition , efficient workflow optimization streamlines processes, allowing businesses to focus on advancement and progress. Efficient certificate governance emerges as a critical component in the domain of electronic protection, enabling organizations to proficiently control their cryptographic assets. Keytalk's state-of-the-art solutions minimize the difficulties of managing digital certificates, facilitating business focus on expansion without risking security. Notable elements of Keytalk's streamlined certificate management consist of: Such improvements allow for a more flexible and safe digital landscape, paving the way for boosted operational capability. While many organizations endeavor to enhance their digital security measures, deploying effective security measures remains a crucial challenge. Keytalk addresses this issue through advanced solutions that fortify public key infrastructure (PKI) systems. By integrating cutting-edge secure encryption methods and login verification processes, Keytalk guarantees that sensitive data remains protected against emerging threats. Their offerings are aimed at enhancing security frameworks, adjusting dynamically to new threats and regulatory standards. Additionally, Keytalk's innovative approach includes real-time monitoring and incident response capabilities, enabling organizations to swiftly identify and mitigate threats to security. This proactive stance not only safeguards digital assets but also fosters trust among stakeholders, thereby contributing to overall online advancement in an increasingly interconnected landscape. Optimized workflow automation represents a transformative approach for organizations seeking to improve their operations. Keytalk’s cutting-edge solutions streamline processes, guaranteeing a seamless integration of Public Key Infrastructure (PKI) into daily workflows. With automation, organizations are able to attain: Such benefits empower organizations to improve productivity and emphasize strategic projects, fostering digital growth while maintaining a secure infrastructure. The innovations from Keytalk highlight the effectiveness of efficient workflow automation in current corporate settings. Controlling electronic certificates skillfully is necessary for ensuring reliability and security in virtual transactions. Organizations face difficulties in managing a increasing number of certificates across different environments. Streamlining credential management involves implementing systematic processes that facilitate the processes of issuance, renewal, and revocation. A unified approach allows for better visibility and control, reducing the risk of lapsed certificates that can lead to service disruptions. Simplified certificate management increases governance and insight, lessening the likelihood of expired certificates and stopping service disruptions. By sorting certificates according to their functionality and relevance, organizations can streamline management activities and allocate resources optimally. Incorporation with present IT systems strengthens the entire workflow, ensuring that each party is aware and on the same page. At the end of the day, streamlined certificate management not only reinforces security but also supports organizational agility in an increasingly virtual environment. A considerable amount of security breaches results from incorrect actions in certificate management processes. Automated systems offers a robust solution to mitigate these vulnerabilities by cutting down on human intervention. By implementing automated systems, organizations can effectively minimize errors and elevate productivity. The primary benefits of automation include: With businesses increasingly depending on digital assets for their operations, upgrading safety precautions becomes paramount to protect sensitive information from evolving threats. Establishing strong security measures like encryption and multi-factor authentication reduces risks related to data breaches. Entities must also prioritize 24/7 monitoring and risk assessment systems to find flaws before they are exploited. Routine audits and compliance assessments are crucial to guarantee that security protocols stay robust against emerging risks. In addition, staff training on security awareness fosters a culture of vigilance, reducing the likelihood of human oversight. Keytalk helps businesses to promote innovation and growth by refining their virtual identity and permission management systems. Utilizing cutting-edge technologies, Keytalk improves organizational efficiency and promotes digital innovation. Organizations can look for the following benefits: With these advantages, Keytalk allows organizations to adapt and succeed in an increasingly digital landscape, encouraging enduring growth and strategic advantage. Multiple industries can greatly benefit from PKI systems automation, particularly the medical field, banking, and technological advancements. In the realm of healthcare, it ensures protected patient data exchanges, while the financial sector uses it to secure transactions and meet regulatory requirements. The technology field applies PKI for the purpose of securing communications and defending intellectual property. Additionally, sectors like government and telecommunications capitalize on PKI automation to enhance security protocols, optimize processes, and augment overall digital trust in their operations. Keytalk works harmoniously with established systems by implementing widely used protocols and APIs, permitting quick communication and data flow. This compatibility guarantees that organizations can incorporate Keytalk’s solutions without significant disruptions to their current workflows. Additionally, its scalable structure supports scalability, enabling businesses to tailor the integration to their specific needs. Through these features, Keytalk enhances overall system performance while maintaining a secure framework for digital growth and identity management. Implementing Keytalk products can resemble the complexity of piecing together an elaborate puzzle. The cost varies according to the dimensions of the organization, particular needs, and alignment with current infrastructure. As a rule, organizations must prepare for expenses related to software licensing, integration services, and sustained assistance. Factors such as the size of launch and tailoring also affect the overall investment. It is recommended to have a thorough consultation to obtain a tailored estimate that aligns with the organization's individual aims and needs. Automating PKI can certainly be tailored to satisfy particular organizational goals. Various solutions provide flexibility in configuration, facilitating the adaptation for businesses the automation process following their particular security mandates, task flows, along with compliance requirements. This alteration might improve productivity and efficacy in managing digital certificates, ensuring that the PKI system fits well with the organization's operational goals. Ultimately speaking, the capability of PKI tech automation serves as an necessary asset for diverse use cases. In a time when rotary phones belong to history, the importance of support after implementation should not be underestimated. Keytalk ensures significant support post-deployment of its solutions. This includes assistance with problems, frequent updates, and educational sessions for users to guarantee effortless integration and operation. Users reap the rewards of dedicated support teams set to handle all issues and refine system operation, guaranteeing a smooth changeover and continued achievement in their digital efforts. In conclusion, embracing PKI tech through Keytalk's innovative solutions not only fortifies security but also drives significant digital growth. While some may argue that automation could introduce new complexities, the streamlined certificate handling and reduction of manual errors ultimately create a more efficient and secure environment. By investing in advanced PKI tools, organizations can confidently navigate the digital landscape, ensuring their assets are protected while fostering innovation and growth in an increasingly competitive market.Elevate PKI Automation for Digital Development – Ensured by Keytalk
Important Insights
An Overview of Public Key Infrastructure (PKI)
The Importance of PKI Automation
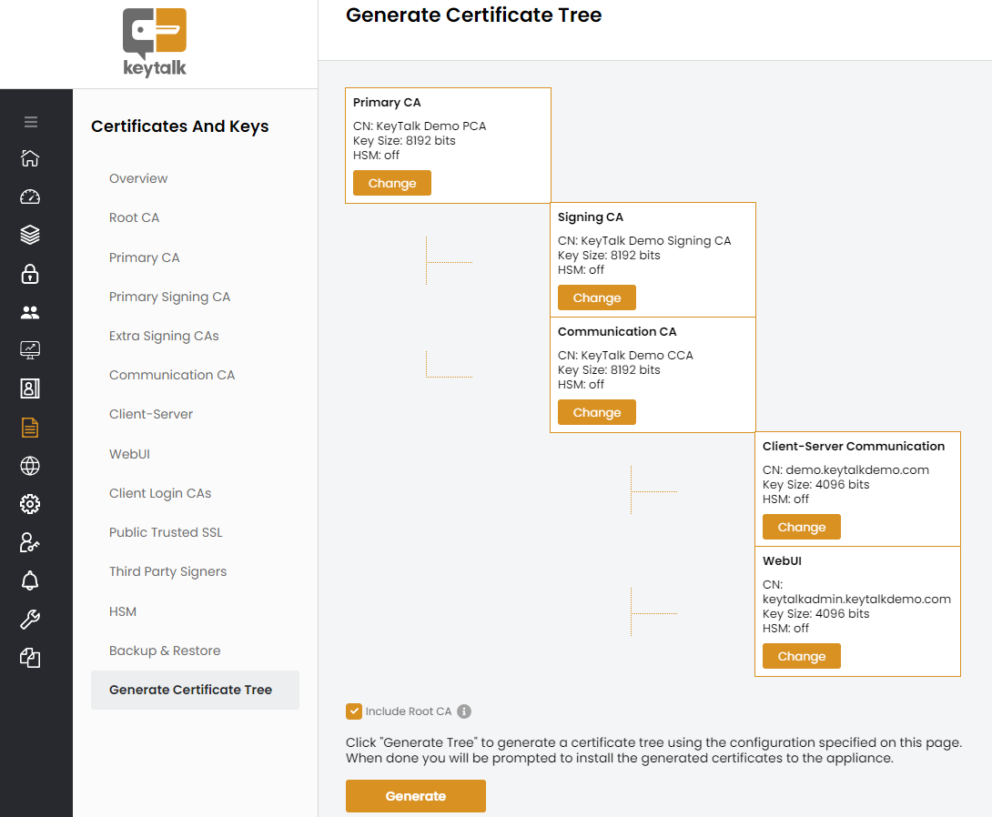
Streamlined Certificate Management
Advanced Protection Methods
Reduced Operational Costs
Innovative Solutions from Keytalk
Effortless Certificate Handling
Reinforced Protection Standards
Productive Workflow Automation
Improving Certificate Management
Reducing Manual Errors With Automation
Enhancing Security for Digital Assets
Propelling Growth and Innovation Using Keytalk
Frequently Inquired Questions
Industries That Stand To Gain The Most From PKI Automation
What Is Keytalk's Integration Process With Current Systems?
How Much Does It Cost to Implement Keytalk Solutions?
Is It Possible to Adapt PKI Automation for Individual Needs?
What Help Is Available from Keytalk Following Implementation?
Conclusion